-
Notifications
You must be signed in to change notification settings - Fork 28
Using GPG Sync in Qubes with Split GPG
If you're a Qubes user and also a PGP user, chances are you use Split GPG, storing your GPG keyring in a vault without internet access. This makes GPG Sync slightly harder to use, because it clearly requires internet access to regularly fetch new public keys from keylists.
One way to make GPG Sync work in your environment is to run it in an AppVM that does have internet access, and set up a scheduled script to regularly copy your public keys into your vault GPG AppVM. These instructions assume that the VM you'd like to run GPG Sync in is called email (this can be the same VM you use an email client like Thunderbird in), and your GPG VM is called gpgvm. If your VMs have different names, make sure to use those instead.
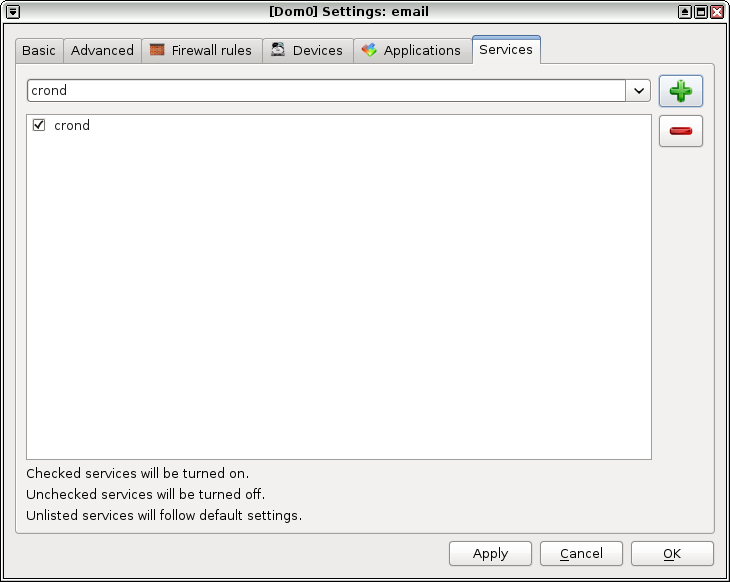
Open Qubes Settings for your email AppVM, switch to the Services tab, select crond from the dropdown and click the "+". Click Ok. This will make the crond service automatically start every time you reboot. When you're done, reboot your email VM and you should now be able to make cron jobs.
Open a terminal in dom0, and as root, edit /etc/qubes-rpc/policy/qubes.GpgImportKey. Add this line to to the top of that file (and change the AppVM names, if necessary), and save and exit:
email gpgvm allow
Now, your email AppVM will be able to copy keys into gpgvm's GPG keyring without having a dom0 window pop up asking which VM you want to import to each time.
In your email AppVM, create a script that exports all of your public keys to a file and then imports them into your GPG VM. Call it /usr/local/bin/gpgsync-copy-to-gpgvm.sh. Here is a script that does that:
#!/bin/bash
export QUBES_GPG_DOMAIN=$(/usr/bin/cat /rw/config/gpg-split-domain)
PUBKEYS=/tmp/pubkeys.asc
/usr/bin/gpg2 --armor --export > $PUBKEYS
/usr/bin/xterm -display :0 -e "/usr/bin/qubes-gpg-import-key $PUBKEYS; sleep 10"
rm $PUBKEYSNote that this script will pop up an xterm window showing you the progress of the import, then wait 10 seconds and close that window. If you'd prefer to this be done entirely in the background, change the line that starts with /usr/bin/xterm to just this:
/usr/bin/qubes-gpg-import-key $PUBKEYSMake sure it's executable:
sudo chmod +x /usr/local/bin/gpgsync-copy-to-gpgvm.sh
Also, make sure that you have a file called /rw/config/gpg-split-domain that contains the name of your GPG VM in it (such as gpgvm). This is described in the official Qubes Split GPG documentation.
Now, create the cron job. As your normal user, run:
crontab -eIn the editor, add the following line, and then save and quit. (In this case, the script is scheduled to run twice a day, at 10am and at 5pm. Adjust it to whatever times you'd like it to run.)
00 10,17 * * * /usr/local/bin/gpgsync-copy-to-gpgvm.sh
Now, public keys you get through GPG Sync will automatically end up in your GPG VM.